Need good Hacking software for gaining access to restricted files? Here is a list of top 10 Hacking software.
Related:
There are Hacking Software for Laptop, Hacking Software for Windows 7, Hacking Software for Windows 8, Hacking software download, free PC to Mobile, Hacking software download, free for Windows XP, Hacking software free for Mobile and Free Hacking Software for PC.
Spyic Gmail TrackerSpyic is another well-known software you can use to crack someone’s Gmail account. It is user-friendly so you will not have any problem to spy on your target. It is fully functional on both iOS. Restore your Gmail Password from Chrome/Firefox Browser. Once you have automatically logged in to your Gmail account with Chrome/Firefox browser on your computer, you can easily view and manage the saved password now. Here I'll show you how to crack a Gmail password from the Chrome browser. Step 1 Input 'chrome://settings/' on your Chrome first. Keylogging: Easiest Way to Hack Gmail Password Keylogging is by far the easiest way to hack Gmail account. Keylogging involves the use of a small software program called the keylogger. This keylogger when installed on a given computer or a cell phone will capture each and every keystroke typed on the keyboard including Gmail and all types of passwords.
1. Nmap- Simple Hacking Software
Download this simple software to uncover bugs on your PC and fix them

- Easy user interface and widely used
- Provides for port scanning and fingerprint detection
- Also provided for OS detection, scanning an IP range and alive hosts
- Rich command mode for advanced users which can combine several commands together
- Hosts its Google opensource project every year.
- Completely free with no additional costs for upgrade.
2. SuperScan- Free Hacking Software
Download this basic software for a cool scanning experience
- Superior scanning speed
- Unlimited support for IP ranges
- Improved host detection using diverse ICMP methods
- TCP SYN scanning incorporated
- Two methods of UDP Scanning’
- IP address import supporting ranges and CIDR formats
- Simple HTML report generation
- Source port scanning’
- Fast Hostname resolving
- Extensive banner grabbing
3. Cain and Abel- Password Hacking Software
This software doubles up as a password recovery tool for Microsoft Operating Systems
- WEP Cracking
- Speeds up packet capture speed through wireless packet injection
- Records VOIP conversations
- Decodes scrambled passwords
- Reveals password boxes
- Uncovers cached passwords
- Dumps protected storage passwords
4. John the Riper- Useful Hacking Software
This useful hacking software is primarily used for cracking passwords open.
- Available for many flavors of Unix, DOS, Win32, BeOS and Open VMS
- Supports Kerberos AFS and Windows NT/2000/XP/2003 LM Hashes
- Has its own highly optimized modules for different hash types and professor architectures
- Additional assembly language routines for several professor architectures, most importantly for x86-64 and x86 with SSE2
- When running on Linux distributions with glibc 2.7+, John additionally supports SHA-crypt hashes, with optional OpenMP parallelization
- Running on recent versions of Solaris, John supports and auto detects SHA-crypt and SunMD5 hashes, also with optional OpenMP parallelization.
5. FS Crack- An advanced hacking software
This advanced software serves as a front for John the Riper.
- Provides a Graphical User Interface for access to most of John’s functions
- Increases the functionality of John the Riper
- Provides detailed reports of password cracks
- Makes use of the SAM file of windows to by-pass password restrictions.
- Completely free and 100% safe and virus free.
6. Nessus Security Scanner- Hack-facilitating software
This is a network administration software which comes in a free trial version following the expiry of which it needs to be purchased.
- Features active scanners, high speed discovery, configuration auditing asset profiling, sensitive data discovery and vulnerability assessment of your security
- The scanners can be disseminated throughout an entire enterprise inside DMZs and across physically separate networks
- Functions in any environment- cloud, hybrid or on-premises
- Supports multiple technologies, more than any other vendor
- Scale of operations vary from the smallest to the largest organizations
- Comes in 4 versions- Nessus home which is free, Nessus Proffessional which needs to be purchased, Nessus Manager which has a free trial and Nessus Cloud which again needs to be purchased.
7. Wireshark-Network Protocol Analyzer
This software is a GTK+ based network protocol analyzer or sniffer that lets you capture and interactively browse the contents of network frames.
- Deep inspection of multiple protocols
- Live capture and offline examination
- Default three pane browser packet
- Runs on multiple platforms including Linux, OS X, Solaris and others
- Powerful display filters
- Exquisite VoIP analysis
- Reads and writes on many different capture file formats
- Coloring rules applicable to the packet list for quick analysis
- Output exported to XML, Postscript, CSV or plain text.
8. Live Bulk Mailer- Bulk Email application
This software is a professional high-performance bulk email software.
- Defaces spam filter of Gmail, Yahoo and Hotmail.
- Offers your proxy servers to hide your IP addresses
- Completely free of cost and no extra cost for upgradation
- Manages opt-in mailing lists for your subscribers
- Creates highly personalized HTML newsletters and messages to transfer them in quick time.
- Consists of an email tracking function
9. Website Digger-Secure Hacking Software
This software searches Google’s cache to search for vulnerabilities, anomalies, configuration issues, proprietary information and unique security snippets.
- Improved user interface in comparison to other hacking softwares
- Does not require Google API License Key
- Compatible with Proxy and TOR
- Analysis of results in real time.
- Result set which can be easily configured
- Signatures are updated.
- Unique ability to save signature selection and result set.
10. Putty- Free Telnet Client for Windows
This software is a free implementation of Telnet and SSH FOR Win32 and Unix platforms.
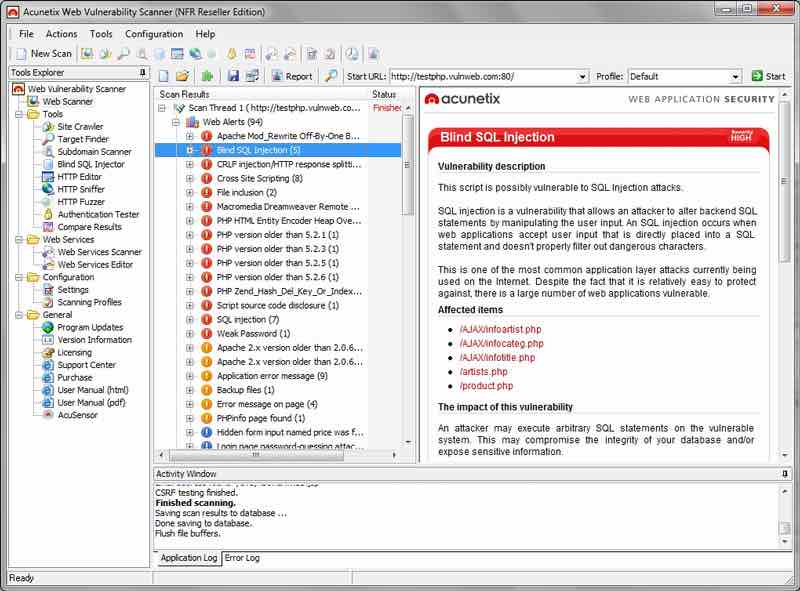
- Supports multiple variations on the secure remote terminal
- Provides user control over SSH encryption key and protocol version
- Authenticates alternate ciphers such as 3DES, Arcfour, Blowfish and DES.
- Emulates control sequences from xterm AND VT102
- Allows Local, remote or dynamic port forwarding with SSH
Thus, with our completely safe and secure hacking softwares, you can now have a crash course in the art of hacking right from the precincts of your home!
Related Posts
Gmail is one of the most popular and most widely used free email service.
But is also frequently targeted by hackers. Much of the time, users might not even realize that someone has hacked their Gmail account.

There are some actions which a hacker can take that will allow him/her to be able to read your email without logging into your Gmail account.
These include using Gmail for mobile, the IMAP feature, email forwarding, and so on. While Gmail’s “last account activity” feature can be helpful, there are other methods of looking into the safety of your Gmail account and keeping it protected.
In today’s post, we will look at some of the easiest ways to find out if your Gmail account has been hacked or compromised. These tips will be useful to all Gmail users including those with no current problems as it is always a superb idea to monitor your email accounts and to know how to monitor unusual activities.
When working online, the first thing we need to be aware of is security.
I was talking to a friend who is a self-proclaimed “hacker”, and I found our conversation to be very interesting. Of particular interest to me was when he was telling me about “social engineering” and how easily he can hack a Gmail or Facebook account. (One of the easiest methods used by my hacker friend involves Gmail fake pages.)
Fortunately, he also mentioned that it is easy to find out if your Gmail account has been hacked using no 3rd party tools.
While I will not go into detail regarding how or why my friend is hacking email addresses, I will share a couple of quick tips which you can use to monitor whether your Gmail account is being hacked. This will teach you how to protect your Gmail accounts. Let’s have a look:
3 Ways of Checking to See if Gmail is Being Hacked:
Contents
- 3 Ways of Checking to See if Gmail is Being Hacked:
1. Check Gmail last account activity feature:
Gmail introduced their last account activity feature a long time ago. “Last account activity” shows the location, IP, method, and time when your Gmail was last accessed. It shows the last 10 logins along with the current login.
So the first thing you should do if you are interested in monitoring the activity of your Gmail account is click on “last account activity” at the bottom of your Gmail account page and check to see when and where your Gmail account was last accessed.
This will give you an idea of whether your Gmail account is being used by someone other than you. You can also log out any other users who may be logging in from another system using this “last account activity” page.

2. Check Email forwarding:
This is another useful feature offered by the Gmail team which allows us to forward any email coming into our Gmail account to any other account.
Gmail Hacking Software For Mac Windows 7
Hackers usually forward all emails to their own accounts and since this feature is not widely known or used, people rarely realize that someone else is reading their email.
You can go to the forwarding page to check to see if your email is being forwarded to any other email address.
3. Check POP and IMAP settings for Gmail:
IMAP and POP features will allow you to access your email on any 3rd party client using any of these two protocols. The issue here is that anyone can configure their email client to receive your email if they get access to your password. This means that a hacker will also be receiving your emails.
If you are not using the IMAP or POP feature, it’s better to keep them disabled. Also make sure you follow step one (noted above) as you may be able to see some unexpected locations and IP addresses if a hacker has already configured his/her email client using your Gmail account.
If you ever have concerns that someone has hacked your Gmail account, you should change your password immediately, along with your security question, password recovery email, and registered phone number. If you are not using 2-factor authentication yet, start using it from now on. This one feature will make your Gmail account 200% secure.
Password Hacking Software For Mac
It’s not a terrible idea to be paranoid about your online security, as you can never be too confident about your preventative measures. It’s better to keep a close eye on your accounts for any unusual activities, and if you give anyone access to your Gmail account, make sure you read reviews and feedback from online communities prior to doing so. Read this guide to learn more about it.
Have you spotted anything unusual suggesting that your Gmail account may have been hacked? Let us know using the comments section below.
Usb Hacking Software Download
If you find the information in this post useful, please share it with your friends and colleagues on Facebook, Twitter, and LinkedIn.